#NMap scripts
Explore tagged Tumblr posts
Text
Basic Linux Security (Updated 2025)
Install Unattended Upgrades and enable the "unattended-upgrades" service.
Install ClamAV and enable "clamav-freshclam" service.
Install and run Lynis to audit your OS.
Use the "last -20" command to see the last 20 users that have been on the system.
Install UFW and enable the service.
Check your repo sources (eg; /etc/apt/).
Check the /etc/passwd and /etc/shadow lists for any unusual accounts.
User the finger command to check on activity summaries.
Check /var/logs for unusual activity.
Use "ps -aux | grep TERM" or "ps -ef | grep TERM" to check for suspicious ongoing processes.
Check for failed sudo attempts with "grep "NOT in sudoers" /var/log/auth.log.
Check journalctl for system messages.
Check to make sure rsyslog is running with "sudo systemctl status rsyslog" (or "sudo service rsyslog status") and if it's not enable with "sudo systemctl enable rsyslog".
Perform an nmap scan on your machine/network.
Use netstat to check for unusual network activity.
Use various security apps to test you machine and network.
Change your config files for various services (ssh, apache2, etc) to non-standard configurations.
Disabled guest accounts.
Double up on ssh security by requiring both keys and passwords.
Check your package manager for any install suspicious apps (keyloggers, cleaners, etc).
Use Rootkit Scanners (chkrootkit, rkhunter).
Double SSH Security (Key + Password).
Disabled Guest Accounts.
Enabled Software Limiters (Fail2Ban, AppArmor).
Verify System Integrity via fsck.
Utilize ngrep/other networking apps to monitor traffic.
Utilize common honeypot software (endlessh).
Create new system-launch subroutines via crontab or shell scripts.
Ensure System Backups are Enabled (rsnapshot).
Check for suspicious kernel modules with "lsmod"
#linux#security#linuxsecurity#computersecurity#networking#networksecurity#opensource#open source#linux security#network#ubuntu#kali#parrot#debian#gentoo#redhat
175 notes
·
View notes
Text
Something I thought of only after sending my last post about programming. Programming in movies and shows (mostly it comes up in tv) is pretty inaccurate in a lot of places. I can think of a few times they got it right:
Hackers. Nearly everything in that movie in terms of how hacking actually works is pretty accurate, especially since most of it is using social engineering to steal people's passwords. They don't build some complicated program to take down the internet or whatever, they write a basic script to just steal as much data as possible.
Matrix Reloaded. Trinity uses nmap (a real UNIX utility program) to scan a server and notices that SSH is running. Then she uses sshnuke to exploit a bug in the server that gives her admin access. The bug and the script to exploit it are both real (the exploit has been patched in real life a while ago).
There's nothing flashy about any of this so it's not too interesting for an audience. That's why you never see it. Same reason even experienced sword fighters like to hit each other's swords in movies: it's less accurate but it's more fun to watch.
#movie#cinema#film#hackers#the matrix reloaded#trinity#nmap#unix#sshnuke#programming#tv#Inaccurate but flashy swordfighting is called Flynning
9 notes
·
View notes
Text
Matrix Breakout: 2 Morpheus
Hello everyone, it's been a while. :)

Haven't been posting much recently as I haven't really done anything noteworthy- I've just been working on methodologies for different types of penetration tests, nothing interesting enough to write about!
However, I have my methodologies largely covered now and so I'll have the time to do things again. There are a few things I want to look into, particularly binary exploit development and OS level security vulnerabilities, but as a bit of a breather I decided to root Morpheus from VulnHub.
It is rated as medium to hard, however I don't feel there's any real difficulty to it at all.
Initial Foothold
Run the standard nmap scans and 3 open ports will be discovered:
Port 22: SSH
Port 80: HTTP
Port 31337: Elite
I began with the web server listening at port 80.

The landing page is the only page offered- directory enumeration isn't possible as requests to pages just time out. However, there is the hint to "Follow the White Rabbit", along with an image of a rabbit on the page. Inspecting the image of the rabbit led to a hint in the image name- p0rt_31337.png. Would never have rooted this machine if I'd known how unrealistic and CTF-like it was. *sigh*
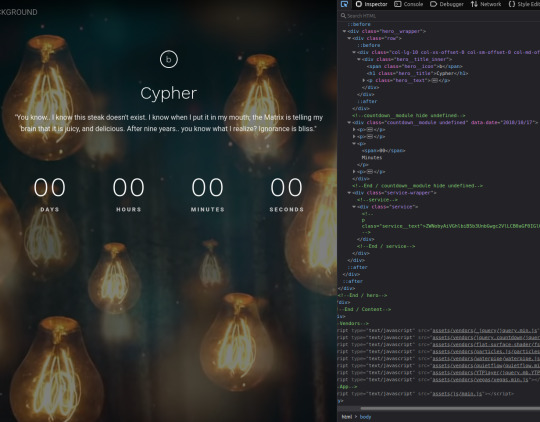
The above is the landing page of the web server listening at port 31337, along with the page's source code. There's a commented out paragraph with a base64 encoded string inside.
The string as it is cannot be decoded, however the part beyond the plus sign can be- it decodes to 'Cypher.matrix'.

This is a file on the web server at port 31337 and visiting it triggers a download. Open the file in a text editor and see this voodoo:
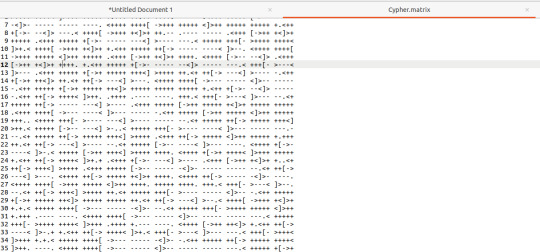
Upon seeing the ciphertext, I was immediately reminded of JSFuck. However, it seemed to include additional characters. It took me a little while of looking around before I came across this cipher identifier.

I'd never heard of Brainfuck, but I was confident this was going to be the in-use encryption cipher due to the similarity in name to JSFuck. So, I brainfucked the cipher and voila, plaintext. :P
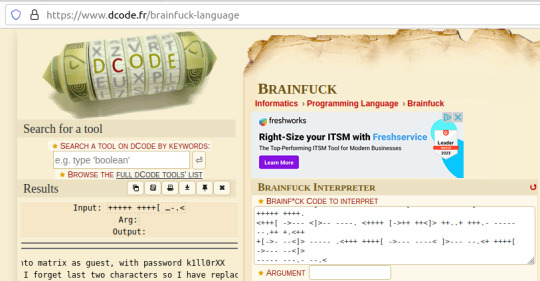
Here, we are given a username and a majority of the password for accessing SSH apart from the last two character that were 'forgotten'.
I used this as an excuse to use some Python- it's been a while and it was a simple script to create. I used the itertools and string modules.
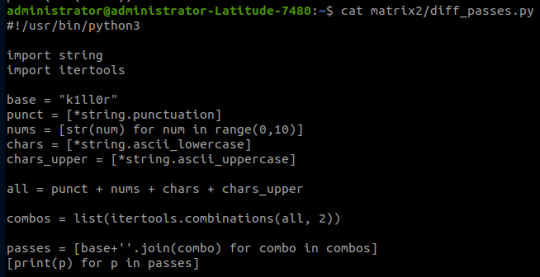
The script generates a password file with the base password 'k1ll0r' along with every possible 2-character combination appended. I simply piped the output into a text file and then ran hydra.
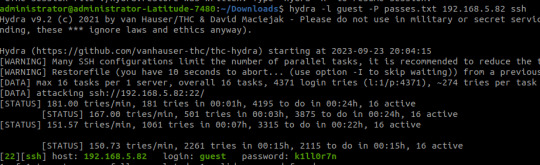
The password is eventually revealed to be 'k1ll0r7n'. Surely enough this grants access to SSH; we are put into an rbash shell with no other shells immediately available. It didn't take me long to discover how to bypass this- I searched 'rbash escape' and came across this helpful cheatsheet from PSJoshi. Surely enough, the first suggested command worked:

The t flag is used to force tty allocation, needed for programs that require user input. The "bash --noprofile" argument will cause bash to be run; it will be in the exec channel rather than the shell channel, thus the need to force tty allocation.
Privilege Escalation
With access to Bash commands now, it is revealed that we have sudo access to everything, making privilege escalation trivial- the same rbash shell is created, but this time bash is directly available.

Thoughts
I did enjoy working on Morpheus- the CTF element of it was fun, and I've never came across rbash before so that was new.
However, it certainly did not live up to the given rating of medium to hard. I'm honestly not sure why it was given such a high rating as the decoding and decryption elements are trivial to overcome if you have a foundational knowledge of hacking and there is alot of information on bypassing rbash.
It also wasn't realistic in any way, really, and the skills required are not going to be quite as relevant in real-world penetration testing (except from the decoding element!)
#brainfuck#decryption#decoding#base64#CTF#vulnhub#cybersecurity#hacking#rbash#matrix#morpheus#cypher
9 notes
·
View notes
Note
Hey wanted to reach out since I've seen you're a woman in cyber too. I was wondering if you knew of any courses/training material that could get me up to speed with using certain CLI tools? Mainly since I'll need it to do config reviews of certain cloud stacks; I'm moving from GRC to a tech/architecture type role and trying to do the reviews manually is a total pain : ( Any tips are appreciated :)
Hi! So I don't do any cloud management, but I have a trick and a more serious qdvice. Idk if it's applicable or not.
1. I memorise commands generally by remembering their meanings.
So for example we have nmap [IP] -sV -vv -p 15-3200 I think of -Service Version -Very Verbose -[Port range]. I also generally build my own cheat sheet based on the commands I use the most.
2. You learn how to write scripts. That's actually very doable. With a very powerful but easy language like python (but there are others!) You can build small programs to automate the process of getting the information you need. For example you could write a program that does a preliminary check, if this check hits some conditions it could perform other checks until it reaches the exit of the program. I cannot write the diagram rn I'm on mobile but if I had to check if something it's working or not this is how I would solve it
Automation is definitely not my area of expertise though, I have two people on the team that do exactly this stuff only.
2 notes
·
View notes
Text
Python for Cybersecurity: Tools and Techniques
With cyber threats growing more sophisticated every day, the demand for skilled cybersecurity professionals is on the rise. Whether it’s protecting networks, detecting malware, or automating security tasks, the tools used in cybersecurity need to be both powerful and flexible. That’s where Python comes in. Known for its simplicity and wide range of applications, Python has become a go-to language for many cybersecurity experts. If you're looking to build a career in this exciting field, enrolling in the best Python training in Hyderabad can set you on the right path.
Why Do Cybersecurity Experts Use Python?
Python is incredibly beginner-friendly, yet powerful enough for advanced security tasks. Its clean syntax makes it easy to write and understand scripts, even for those new to programming. Plus, it supports a vast ecosystem of libraries that are perfect for tasks like data analysis, network monitoring, and penetration testing.
But the real magic lies in how fast you can get things done with Python.Want to scan for vulnerabilities with a quick script? Or automate a log monitoring task? Python makes it simple and efficient.
Popular Python Tools in Cybersecurity
Here are some of the most commonly used Python tools in the cybersecurity world:
Scapy: Great for analyzing and crafting network packets.
Requests & BeautifulSoup: Used for web scraping and identifying website vulnerabilities.
Nmap (via python-nmap): Integrates the popular network scanning tool with Python for custom automation.
Impacket: Provides tools to interact with network protocols at a lower level.
Cryptography & PyCrypto: Essential for data encryption and building secure systems.
These tools are widely used in real-world scenarios to monitor traffic, detect attacks, and strengthen system defenses.
Ethical Hacking and Automation with Python
System vulnerabilities are often tested using Python by ethical hackers. Whether it's writing a brute-force attack script or building a port scanner, Python gives security professionals the power to simulate attacks and patch weaknesses before real hackers can exploit them.
Python is also perfect for automating routine security tasks���like scanning logs or monitoring files—freeing up professionals to focus on more critical threats.
Ready to Learn? Start with SSSIT Computer Education
If you're serious about launching a career in cybersecurity, Python is a must-have skill. At SSSIT Computer Education, we offer hands-on, job-ready Python training designed to help you succeed in the real world. Our expert instructors and practical approach make us one of the top choices for aspiring cybersecurity professionals in Hyderabad.
#best software training in hyderabad#best software training in kukatpally#best software training in KPHB#Best software training institute in Hyderabad
0 notes
Text
Scripts Úteis do Nmap para Hackers Éticos
Por Rodrigo Carran O Nmap (Network Mapper) é uma ferramenta de linha de comando open-source para Linux usada para escanear endereços IP, portas em uma rede e detectar aplicativos instalados. Administradores de rede usam o Nmap para identificar dispositivos, portas abertas, serviços em execução e vulnerabilidades. A sintaxe básica do Nmap é: nmap <ip/url> Vamos fazer um teste rápido no…
View On WordPress
0 notes
Text
Navigating Ethical Hacking: Five Steps for Success
In our increasingly digital world, ethical hacking is a critical skill for safeguarding sensitive information and systems. Ethical hackers, or "white hats," play a vital role in identifying vulnerabilities before they can be exploited by malicious actors. Here, we outline five essential steps for success in ethical hacking.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Ethical Hacking Course in Chennai

1. Build a Strong Foundation in Networking and Security
Before diving into ethical hacking, it’s essential to have a solid grasp of networking and cybersecurity principles. Understanding how networks operate and the basics of security will set you up for success.
Key Areas to Focus On:
Network Protocols: Familiarize yourself with TCP/IP, DNS, and HTTP.
Security Concepts: Learn about firewalls, intrusion detection systems, and encryption methods.
Resources:
Online courses (e.g., Coursera, Udemy)
Books like "CompTIA Network+ Guide to Networks"
2. Master the Tools of the Trade
Ethical hackers use a variety of tools to assess security vulnerabilities. Familiarizing yourself with these tools is crucial for effective testing.
Must-Know Tools:
Nmap: For network discovery and scanning.
Metasploit: A framework for developing and executing exploit code.
Wireshark: For network protocol analysis.
Practice:
Hands-on experience is vital. Set up a lab environment to experiment with these tools.
3. Learn Programming and Scripting
Understanding programming is essential for ethical hackers. It enables you to write scripts, automate tasks, and understand how applications can be exploited.
Recommended Languages:
Python: Great for scripting and automation.
JavaScript: Important for web application testing.
Bash/Shell: Useful for command-line tasks and automation.
Resources:
Online coding platforms (e.g., Codecademy, freeCodeCamp)
Books like "Automate the Boring Stuff with Python"
With the aid of Best Online Training & Placement programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
4. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly evolving. Staying updated on the latest threats, vulnerabilities, and hacking techniques is crucial for success.
How to Stay Informed:
Follow Blogs and News Sites: Websites like Krebs on Security and Threatpost.
Engage with Communities: Join forums and groups on platforms like Reddit and LinkedIn.
Attend Conferences: Participate in cybersecurity conferences and workshops.
5. Practice Ethical Hacking Regularly
The best way to hone your skills is through regular practice. Engaging in Capture The Flag (CTF) challenges and using platforms designed for ethical hacking can provide valuable experience.
Recommended Platforms:
Hack The Box: A platform for practicing penetration testing.
TryHackMe: Offers guided learning paths for various skills in cybersecurity.
Focus:
Set up personal projects or participate in ethical hacking competitions to apply what you’ve learned.
Conclusion
Navigating the world of ethical hacking requires dedication, continuous learning, and practice. By building a strong foundation in networking, mastering essential tools, learning programming, staying updated on trends, and practicing regularly, you can set yourself up for success in this dynamic field. Embrace the challenge and contribute to making the digital world a safer place!
0 notes
Text
Les 7 applications Android que tout hacker éthique doit avoir
L’univers de la cybersécurité évolue rapidement, et avec lui, les outils à la disposition des hackers éthiques. Que vous soyez débutant souhaitant apprendre les bases du hacking ou professionnel expérimenté en quête de solutions mobiles performantes, il existe aujourd’hui des applications Android puissantes qui vous permettent d’analyser, protéger et tester la sécurité d’un réseau ou d’un système directement depuis votre smartphone. Dans cet article, je vous présente les 5 meilleures applications Android que tout hacker éthique doit avoir, utilisables sans PC. 1. Termux – Le terminal Linux dans votre poche Pour tout hacker éthique, la maîtrise de la ligne de commande est essentielle. C’est là qu’intervient Termux, une application qui vous offre un terminal Linux complet directement sur votre Android, sans root. Avec Termux, vous pouvez : Installer des outils tels que nmap, hydra, ou sqlmap Écrire et exécuter vos propres scripts en Python, Bash, etc. Gérer des paquets via le gestionnaire APT Grâce à sa légèreté et sa compatibilité avec F-Droid, Termux devient le point de départ idéal pour tout environnement de test mobile. 📥 Télécharger Termux sur F-Droid 2. Kali NetHunter – La puissance de Kali Linux sur Android Une fois familiarisé avec l’environnement Linux grâce à Termux, vous pouvez passer à un niveau supérieur avec Kali NetHunter. Développée par Offensive Security, cette plateforme regroupe les principaux outils de test de pénétration dans une interface mobile. Ses atouts : Attaques man-in-the-middle (MITM) Injection de paquets, scan de ports, sniffing réseau Disponible en version rootless Kali NetHunter transforme votre téléphone en un véritable laboratoire de sécurité mobile, sans avoir besoin de rooter votre appareil. 📥 Télécharger Kali NetHunter 3. Orbot – L’anonymat avant tout Lorsque vous effectuez des analyses ou naviguez dans des environnements sensibles, protéger votre identité est crucial. C’est ici qu’intervient Orbot, un proxy mobile qui fait transiter vos données par le réseau Tor. Pourquoi l’utiliser : Masquer votre adresse IP Chiffrer le trafic sortant de vos applications Appliquer Tor à des applis spécifiques via VPN local Combiné à Termux ou NetHunter, Orbot garantit un niveau d’anonymat supplémentaire, indispensable lors de tests d’intrusion en réseau ou sur des applications distantes. 📥 Télécharger Orbot sur le site du Guardian Project 4. Fing – L’analyseur de réseau intelligent Maintenant que votre environnement est sécurisé, il est temps de scanner les réseaux à la recherche de failles potentielles. Fing est l’une des applications les plus complètes pour cette tâche. Fonctionnalités clés : Détection de tous les appareils connectés Analyse des ports ouverts et services actifs Identification des adresses IP, MAC, et constructeurs Fing est extrêmement simple à utiliser et vous permet d’auditer la sécurité d’un réseau Wi-Fi en quelques minutes, directement depuis votre téléphone. 📥 Télécharger Fing sur Google Play 5. FakeTraveler – Falsifiez votre localisation GPS sans root Dans certaines situations, il peut être utile de simuler une autre localisation GPS sur votre smartphone, que ce soit pour préserver votre vie privée, tester des applications sensibles à la géolocalisation ou valider des comportements en conditions simulées. FakeTraveler répond parfaitement à ce besoin en proposant une interface simple et intuitive : Une carte interactive où vous pouvez sélectionner la localisation désirée via un appui long Possibilité d’appliquer la localisation fake immédiatement Options avancées pour simuler la localisation sur une période donnée Pas besoin de root : l’application utilise la fonctionnalité "Mock Location" disponible dans les options développeur Android 📥 Télécharger FakeTraveler sur F-Droid 6. WiFiAnalyzer – Analyse des réseaux Wi-Fi WiFiAnalyzer vous aide à visualiser les réseaux Wi-Fi environnants, identifier les canaux encombrés et optimiser votre propre réseau.
Fonctionnalités principales : Détection des réseaux Wi-Fi à proximité Analyse des canaux pour éviter les interférences Graphiques en temps réel de la puissance du signal 📥 Télécharger WiFiAnalyzer sur Google Play 7. NetHunter Store – Accès à des outils spécialisés Le NetHunter Store est une boutique d'applications basée sur F-Droid, offrant une collection d'outils de sécurité et de hacking éthique, même sans installer Kali NetHunter. Fonctionnalités principales : Accès à des applications comme WiFi Analyzer, cSploit, et plus Téléchargements sécurisés sans télémétrie Interface adaptée aux professionnels de la sécuritéMyGreatLearning 📥 Accéder au NetHunter Store En combinant ces cinq applications, vous disposerez d’un environnement de test de pénétration complet et mobile. ⚠️ Rappel important : n’utilisez ces outils que dans un cadre légal et éthique — par exemple sur votre propre réseau, sur des environnements de test, ou dans le cadre d’un audit autorisé. Le hacking éthique n’est pas un jeu, c’est une discipline sérieuse et précieuse pour la sécurité numérique de tous.
0 notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
Best Tools & Software You Will Learn in an Ethical Hacking Course in CRAFT Dehradun

In today’s digital world, cybersecurity threats are on the rise, making ethical hacking a crucial skill for IT professionals. If you're looking for a top-rated Ethical Hacking Course in Dehradun, CRAFT Empowering Careers offers a hands-on program covering all the essential tools and software used by ethical hackers. Join now and kickstart your journey in cybersecurity!
Why Learn Ethical Hacking?
Ethical hackers play a key role in securing networks, applications, and data from cyber threats. Learning ethical hacking opens doors to exciting career opportunities in cybersecurity, penetration testing, and network security. By enrolling in our Ethical Hacking Course in Dehradun, you'll gain real-world experience with industry-standard tools and techniques.
Essential Tools & Software Covered in the Course
At CRAFT Empowering Careers, our ethical hacking course includes practical training on some of the most powerful tools used in cybersecurity.
1. Kali Linux – The Ultimate Penetration Testing OS
Pre-installed with top security tools like Nmap, Metasploit, and Wireshark.
Used by professionals for ethical hacking and penetration testing.
2. Metasploit Framework – Mastering Exploits
A must-have tool for penetration testers.
Helps in identifying vulnerabilities and launching simulated cyberattacks.
3. Wireshark – The Best Network Analysis Tool
Monitors and captures network traffic to detect unauthorized activities.
Essential for network security assessments.
4. Nmap (Network Mapper) – Scanning & Auditing Networks
Helps in network discovery, identifying open ports, and running security audits.
Used by professionals to map out network vulnerabilities.
5. Burp Suite – Web Application Security Testing
An advanced tool for detecting vulnerabilities like SQL injection and cross-site scripting (XSS).
Essential for web security professionals.
6. Aircrack-ng – Wireless Security Assessment
Tests the security of Wi-Fi networks.
Helps in cracking WEP and WPA-PSK encryption for security analysis.
7. SQLmap – Automated SQL Injection Detection
Detects and exploits SQL injection vulnerabilities in databases.
A must-have tool for database security testing.
8. John the Ripper – Password Cracking Made Easy
Helps test the strength of passwords.
Supports various encryption techniques and algorithms.
9. Nikto – Web Server Security Scanner
Scans web servers for outdated software, misconfigurations, and vulnerabilities.
Ensures website security against cyber threats.
10. Maltego – Cyber Intelligence & Investigation Tool
Used for information gathering and mapping relationships between entities.
Helps cybersecurity professionals in reconnaissance and intelligence gathering.
Enroll in the Best Ethical Hacking Course in Dehradun
At CRAFT Empowering Careers, we provide practical training with real-world hacking scenarios to help you master cybersecurity skills. Our course is designed for beginners and professionals looking to build a strong foundation in ethical hacking.
Key Features of Our Ethical Hacking Course:
✔ Hands-on training with real-world tools.
✔ Expert guidance from cybersecurity professionals.
✔ Certification upon course completion.
✔ 100% placement assistance for career growth.
Enroll Now and take the first step toward a rewarding cybersecurity career!
Conclusion
Cybersecurity is a booming field, and ethical hackers are in high demand. By mastering tools like Kali Linux, Metasploit, Wireshark, and more, you can boost your cybersecurity skills and land high-paying jobs in the IT sector. Join the Ethical Hacking Course in Dehradun at CRAFT Empowering Careers and start your journey today!
For more details, visit: CRAFT Empowering Careers Ethical Hacking Course
0 notes
Text
Ethical Hacker Course: Key Skills You Will Learn
With the increasing number of cyber threats and data breaches worldwide, the demand for skilled ethical hackers is higher than ever since the past two decades. An ethical hacker course equips professionals with the knowledge and hands-on experience needed to identify, exploit, and fix the security vulnerabilities in networks & systems. If you are looking for career in cyber security, here’s a very depth analysis at the important skills you will learn in an ethical hacking course.
Core Modules in an Ethical Hacker Course
An ethical hacking course covers various modules designed to provide a solid foundation in cybersecurity. Some of the core modules include:
1. Introduction to Basics of Ethical Hacking
Understanding the role & responsibilities of an ethical hacker
Legal & ethical considerations in cybersecurity
Different types of cyber threats and attack methodologies
2. Footprinting and Reconnaissance
Gathering information about a target system using open-source intelligence (OSINT)
Using tools like Nmap, Maltego, and Google Dorking to identify vulnerabilities
Techniques such as passive and active reconnaissance
3. Scanning Networks and System Hacking
Identifying open ports, services, and vulnerabilities
Exploiting security loopholes using vulnerability scanners
Password cracking techniques, privilege escalation, and maintaining access
4. Malware Threats & Attack Vectors
Understanding types of malware: viruses, worms, ransomware, and trojans
Analyzing malware behavior & prevention strategies
Using sandboxing & endpoint protection tools
5. Web Application Security
Detecting common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF)
Security testing methodologies for web applications
Understanding Secure Software Development Life Cycle (SDLC)
6. Wireless Network Security
Understanding Wi-Fi encryption standards (WEP, WPA, WPA2, WPA3)
Conducting wireless penetration testing
Preventing wireless network intrusions
7. Cryptography and Network Security
Basics of encryption, hashing, and digital signatures
Implementing secure communication channels
Understanding of VPNs, firewalls and Intrusion Detection Systems (IDS)
Hands-On Learning: Practical Exercises and Real-World Scenarios
Ethical hacking courses emphasize hands-on learning to prepare professionals for real-world cybersecurity challenges. Some key practical aspects include:
Penetration Testing Labs: Simulated environments where students can practice exploiting vulnerabilities.
Capture The Flag (CTF) Challenges: Gamified cybersecurity competitions to test hacking skills.
Incident Response Simulations: Handling real-world cybersecurity incidents, including data breaches and denial-of-service (DoS) attacks.
Reverse Engineering and Exploit Development: Analyzing malicious code and writing exploits for vulnerabilities.
By working on real-world cybersecurity scenarios, ethical hackers develop real time problem solving skills and learn to think like attackers to defend systems very effectively.
Important Tools & Tactics Used by Ethical Hackers
Ethical hackers used the various tools and techniques to perform security assessments. Some of the essential tools include:
Kali Linux: A penetration testing operating system with a wide range of security tools.
Metasploit Framework: A very powerful tools for developing and executing exploit any code.
Burp Suite: A web vulnerability scanner used for security testing of web applications.
Wireshark: A network protocol analyzer for capturing & analyzing network traffic in the systems.
John the Ripper and Hashcat: Password cracking tools.
Nmap and Zenmap: Network scanning tools for identifying vulnerabilities.
SQLmap: A tool that used for detecting & exploiting My SQL injection vulnerabilities.
Using these tools, ethical hackers perform penetration testing, vulnerability assessments, and forensic analysis to strengthen an organization’s security posture.
Complement Certifications CEH for Career & Growth:
While the Certified Ethical Hacker certification is a highly demanding credential, comparing it with other certifications can further improve your career opportunities. Some of the complementary certifications include:
1. Offensive Security Certified Professional (OSCP)
Focuses & Improve on hands-on penetration testing skills.
Requires candidates to complete a challenging 24-hour practical exam.
Those who are looking to specialize in offensive security.
2. GIAC Penetration Tester (GPEN)
Covers advanced penetration testing techniques.
Recognized by government and enterprise cybersecurity teams.
Focuses on exploit development, privilege escalation, and password attacks.
3. Certified Information Systems Security Professional (CISSP)
Covers broad cybersecurity domains, including risk management and governance.
Ideal for those aspiring to take on security management roles.
Highly valued by employers worldwide.
4. CompTIA PenTest+
Covers penetration testing methodologies, tools, and reporting.
A good alternative for those starting in ethical hacking.
5. EC-Council Certified Security Analyst (ECSA)
Advanced ethical hacking certification that builds on CEH.
Covers in-depth penetration testing methodologies.
Ideal for professionals looking to specialize in vulnerability assessment and red teaming.
Conclusion
An ethical hacker course provides professionals with in-depth knowledge and hands-on experience in cyber security programs. From network scanning and malware analysis to penetration testing and web security, ethical hackers develop a very powerful skill set to protect organizations from cyber threats. With the right combination of certifications and in depth practice, ethical hackers can advance their careers and contribute to strengthening global cyber security defenses. Are you ready to take on your ethical hacking journey? Start learning today and build a rewarding career in cybersecurity!
#ceh certification requirements#ethical hacking course#hacking course#ethical hacking courses#ethical hacker course
0 notes
Text
Crack the Code: How to Bulletproof Your Web Application In today’s hyper-connected world, web applications are the backbone of businesses, enabling seamless user experiences and efficient operations. However, with great convenience comes the looming threat of cyberattacks. From data breaches to phishing schemes, the stakes have never been higher. This is where security testing steps in—a vital process to ensure your web application can withstand malicious attacks. In this comprehensive guide, we’ll walk you through how to perform security testing for web applications effectively. Whether you’re a developer, QA engineer, or project manager, understanding these techniques is crucial to safeguarding your application and user data. 1. Understand the Basics of Security Testing Before diving into the technicalities, it’s essential to grasp what security testing is all about. In a nutshell, security testing evaluates a web application to identify vulnerabilities, weaknesses, and potential entry points for attackers. Why Security Testing Matters: Protects sensitive user data from unauthorized access. Ensures compliance with industry regulations (e.g., GDPR, HIPAA). Maintains the reputation and trustworthiness of your business. Types of Security Testing: Vulnerability Scanning: Identifies known vulnerabilities using automated tools. Penetration Testing: Simulates real-world attacks to find exploitable weaknesses. Security Auditing: Reviews code, configurations, and infrastructure for security flaws. Ethical Hacking: Involves ethical hackers to test your application’s resilience. 2. Prepare for Security Testing Preparation is key to effective security testing. Follow these steps to set the stage: Define Objectives: Determine the scope of your testing. Are you focusing on authentication mechanisms, data encryption, or overall application security? Understand Your Application: Map out the application’s architecture, including its features, data flow, and integration points. This helps in pinpointing areas to test. Gather Tools and Resources: Security testing requires a mix of automated tools and manual techniques. Some popular tools include: OWASP ZAP: Open-source tool for finding vulnerabilities. Burp Suite: Comprehensive platform for security testing. Nmap: Network scanner for identifying open ports and services. Metasploit: Framework for penetration testing. Establish a Test Environment: Create a separate environment for security testing to avoid affecting live users. Use realistic data and configurations to simulate real-world scenarios. 3. Key Areas to Focus On Security testing involves a thorough examination of various aspects of a web application. Below are the critical areas to focus on: Authentication and Authorization: Ensure that users can only access data and features they’re authorized to use. Test login mechanisms for brute-force vulnerabilities. Check session management to prevent session hijacking. Verify role-based access control (RBAC). Input Validation: Validate all user inputs to prevent injection attacks such as SQL injection, cross-site scripting (XSS), and command injection. Use whitelisting instead of blacklisting. Implement input sanitization on both client and server sides. Data Protection: Secure sensitive data both in transit and at rest. Use HTTPS for all communication. Encrypt sensitive information using strong algorithms (e.g., AES-256). Avoid storing unnecessary user data. Error Handling: Ensure error messages do not expose sensitive information. Avoid displaying stack traces or database errors. Log errors for debugging but ensure logs are securely stored. Third-Party Dependencies: Regularly update and audit third-party libraries and APIs to minimize vulnerabilities. Use tools like Dependabot or Snyk to monitor dependencies. 4. Conducting Security Tests
Now that you’re prepared, it’s time to execute the tests. Below are some common techniques: 1. Vulnerability Scanning: Run automated scans to detect common vulnerabilities such as insecure configurations and outdated components. Use OWASP ZAP for a quick and efficient scan. 2. Penetration Testing: Simulate real-world attacks to uncover hidden vulnerabilities. For instance: Attempt SQL injection attacks by inserting malicious SQL queries. Test for cross-site scripting (XSS) by injecting JavaScript code into input fields. 3. Fuzz Testing: Feed your application unexpected or random data to observe how it handles invalid inputs. This can reveal edge cases where your app may crash or behave unpredictably. 4. Secure Code Review: Manually review your application’s source code to find potential security flaws. Pay special attention to authentication logic, input validation, and error handling. 5. Remediation and Reporting Security testing is not just about finding vulnerabilities—it’s about fixing them. Prioritize Vulnerabilities: Use a risk-based approach to address vulnerabilities based on their severity and impact. Focus on critical issues first, such as SQL injection or weak password policies. Implement Fixes: Collaborate with your development team to resolve vulnerabilities. Test the fixes to ensure they work as intended without introducing new issues. Document Findings: Prepare a detailed report summarizing: Vulnerabilities discovered. Steps taken to remediate them. Recommendations for ongoing security practices. 6. Best Practices for Ongoing Security Security is not a one-time activity but a continuous process. Here are some best practices to maintain a secure web application: Adopt the Principle of Least Privilege: Grant users and systems only the access they need to perform their functions. Keep Software Up to Date: Regularly update your web application, server, and dependencies to patch known vulnerabilities. Conduct Regular Security Audits: Schedule periodic reviews to stay ahead of potential threats. Educate Your Team: Train your development and operations teams on secure coding and deployment practices. Monitor and Respond: Use intrusion detection systems (IDS) and log monitoring to identify and respond to suspicious activity in real time. Conclusion Security testing is a vital component of web application development and maintenance. By proactively identifying and addressing vulnerabilities, you not only protect your users but also ensure the long-term success of your application. Whether you’re running a small e-commerce site or a large-scale enterprise platform, investing in robust security practices pays dividends in trust and reliability. So, roll up your sleeves, follow the steps outlined in this guide, and make your web application a fortress against cyber threats.
0 notes
Text

It's time to expand the geographical footprint and leave the neighbors spoofed SSIDs. The opsec needs to be completely flawless going forward. First grab a $200 used ThinkPad with cash from a street vendor with no receipts, no trace, and a USB kill switch. Wipe it clean with DBAN, then hit a library PC to download Tails OS onto a 16GB SanDisk USB, enabling encrypted persistent storage with a 32-character passphrase stored on my X-seed. Boot it at a McDonald’s, USB in, Tor up, and route through a cash-bought VPN. Tweak Tor’s exit nodes with Germany, Netherlands avoiding Five Eyes in the simplest ways. Wi-Fi’s via a $10 dongle in my backpack, MAC spoofed to a random hex via macchanger. My IP’s a ghost. The 20 wallets private keys are offline and handwritten. load five keys into Exodus (checked for no telemetry) on Tails’ persistent storage. Liquidity’s tight for ETH-Monero atomic swaps—Uniswap’s XMR pair is thin, so I spread $10M ETH across 50 Monero wallets, $200K each, using THORChain and Haveno too. I test $500 swaps first, confirm they clear, then ramp up—$50K/hour across five swaps, pausing 2-3 hours between, over 10 days. I would script on Tails with web3.py, generating 500 ETH wallets, private keys dumped to an encrypted VeraCrypt container in persistent storage. I bake in Wireshark, Nmap, tcpdump, Snort, Nikto, Burp Suite, and Kismet.. precompiled binaries from GitLab, verified SHA256 hashes to monitor Tor traffic, scan for honeypots, and sniff Wi-Fi threats. The script drips $10M, $20K per wallet, over 72 hours via Tor bridges (obfs4), randomized delays (5-15 minutes). I send $100 ETH from 50 wallets to noisy sinks like Binance deposit addresses (scraped from Etherscan), OpenSea contracts, and a Ukraine BTC donation wallets with the atomic swapped-fresh ETH adresses, while cross-transacting between my wallets: wallet A to B, B to C, 0.05 ETH each, 200 times. I burn $100K including gas ($20/tx at 50 gwei) over two weeks. Chainalysis drowns in noise. The botnet’s quiet side swaps ETH to Monero $5K-$10K chunks, targeting $1M/month, matching Monero’s $30M daily OI I use Haveno’s escrow, rotate Tor circuits, and pause 2-5 days between bursts. Locations shifts from McDonald’s, Starbucks to co-working spaces in nomad hubs like Bali, cayman, Jersey, Malta, Bermuda, Isle of Man, Cyprus, Bahamas, and Chiang Mai. I spoof the dongle’s MAC daily, monitor with Kismet for IMSI catchers, and never stay longer than 45 minutes. If a network’s crowded, I ping with Nmap.. too many devices, I bounce. Cashout’s the long game… With somewhere around $10M in Monero across 50 wallets annually, I hit OTC via Telegram groups, swapping $10K-$50K for USD or EUR, cash or tether. remain blended in with nomad towns where cash flows. Could even pose as a trust-fund drifter, living off “clean” Solana and BTC wallets funded by Monero swaps, tumbled through Wasabi’s CoinJoin for extra cover. Laptops die after 10 uses and moves quarterly. The other $1.49 billion? It’s staying cold for the long run. Split across 20 32GB USBs, each with 1/20th of the keys in encrypted 7z archives. AES-256 stays locked in safes through various deposit boxes. I clean $20M max annually mby even far lower depending on the OI. Scaling will remain low, otherwise botnets spike bandwidth, swaps dry up, feds get wise n sniff Tor exits. One slip, either be reused bridge, same Wi-Fi SSID twice. I settle in Podgorica, Montenegro: or any country with no US/EU extradition treaties, $500K buys a villa, and $10K/month keeps me invisible. $20m annually is enough to manipulate local surroundings.
1 note
·
View note
Text
Top 5 Cybersecurity Career Paths Worth Pursuing in 2025

The digital world is expanding at an unprecedented rate, and with it, the threats to our data and systems are becoming more sophisticated. This has created a massive and ever-growing demand for skilled cybersecurity professionals. If you're looking for a rewarding and future-proof career, cybersecurity in 2025 offers a wealth of exciting opportunities. Let's explore the top 5 career paths worth pursuing in this dynamic field:
1. Cybersecurity Analyst:
What they do: Cybersecurity Analysts are the first line of defense, constantly monitoring networks and systems for suspicious activity. They analyze security logs, identify potential threats, and respond to security incidents. They play a crucial role in preventing attacks and mitigating damage.
Why it's hot in 2025: With the increasing volume and complexity of cyber threats, every organization needs skilled analysts to keep their digital environments secure. This role is often the entry point into cybersecurity, offering a solid foundation for further specialization.
Key skills: Security Information and Event Management (SIEM), intrusion detection/prevention systems (IDS/IPS), network security principles, threat intelligence analysis, incident response, and strong analytical and problem-solving skills.
2. Penetration Tester (Ethical Hacker):
What they do: Penetration testers, also known as ethical hackers, are hired to legally and ethically simulate cyberattacks on organizations' systems and networks. They identify vulnerabilities before malicious actors can exploit them, providing valuable insights for strengthening security defenses.
Why it's hot in 2025: As attack surfaces expand and become more complex, the need for skilled penetration testers to proactively identify weaknesses is paramount. Their expertise is crucial for preventing costly data breaches and reputational damage.
Key skills: Network security, web application security, operating system security, vulnerability assessment tools (e.g., Metasploit, Nmap), scripting (Python, Bash), and a deep understanding of attack methodologies.
3. Cybersecurity Engineer:
What they do: Cybersecurity Engineers are responsible for designing, implementing, and maintaining an organization's security infrastructure. 1 This includes firewalls, intrusion detection 2 systems, security software, and other security tools. They ensure that security measures are robust, scalable, and effectively protect against threats.
Why it's hot in 2025: With the increasing reliance on cloud computing, IoT devices, and complex network architectures, the demand for skilled engineers who can build and manage secure environments is skyrocketing.
Key skills: Network architecture, security protocols, cloud security (AWS, Azure, GCP), security tool deployment and management, identity and access management (IAM), cryptography, and knowledge of relevant security frameworks and compliance standards.
4. Security Architect:
What they do: Security Architects take a holistic view of an organization's security needs and design comprehensive security strategies and architectures. They assess risks, define security requirements, and develop blueprints for implementing security solutions across the entire IT infrastructure.
Why it's hot in 2025: As organizations grapple with increasingly sophisticated threats and complex regulatory landscapes, the need for strategic thinkers who can design robust and future-proof security architectures is critical.
Key skills: Security frameworks (e.g., NIST, ISO 27001), risk management, security architecture design, cloud security architecture, network security architecture, knowledge of emerging security technologies, and strong communication and leadership skills.
5. Incident Response Specialist:
What they do: When a cyberattack occurs, Incident Response Specialists are the first responders. They are responsible for containing the attack, eradicating the threat, recovering compromised systems and data, and conducting post-incident analysis to prevent future attacks.
Why it's hot in 2025: Despite the best preventative measures, cyberattacks are inevitable. Skilled incident responders are crucial for minimizing the damage and ensuring business continuity when breaches occur.
Key skills: Incident handling methodologies, digital forensics, malware analysis, network security, knowledge of common attack vectors, communication skills, and the ability to remain calm and decisive under pressure.
Level Up Your Career with Xaltius Academy's Cybersecurity Course:
Ready to launch or advance your career in one of these high-demand cybersecurity fields? Xaltius Academy's Cybersecurity Course is designed to equip you with the foundational knowledge and practical skills needed to succeed in this dynamic industry.
Key benefits of the program:
Comprehensive Curriculum: Covers essential cybersecurity concepts and in-demand skills relevant to these top career paths.
Hands-on Training: Provides practical experience through labs, simulations, and real-world scenarios.
Expert Instructors: Learn from industry professionals with years of experience in cybersecurity.
Career Guidance: Offers support and resources to help you navigate the job market and achieve your career goals.
The cybersecurity landscape in 2025 is brimming with opportunities for skilled professionals. By focusing on one of these top career paths and investing in your education with a program like Xaltius Academy's Cybersecurity Course, you can position yourself for a rewarding and impactful future in a field that is vital to our digital world. Don't just secure data; secure your future!
1 note
·
View note
Text

With all the hassles present on the internet, brings forth the importance of cyber security, be it an average citizen an aspiring IT specialist or a student. Every individual can learn the cyber environment and enhance their skills with the right set of tools. Following is a list of free tools for cybersecurity tools every beginner should explore.
1. Wireshark
A hugely potent organized protocol analyzer wireshark enables you to analyze data packets in real times by capturing them. It is an excellent tool for analyzing organized network issues, learning about the functions of networks, and investigating basic-level functions. It can be used by beginners to gain insights on the movement of information across a network and also pinpoint existing potential security issues.
Features:
Pckect analyzing in real-time.
Supports a wide array of protocols.
Easy to use with many visual representations.
2. Nmap (Network Mapper)
A tightly held toolkit for those practicing ethical hacking and penetration testing is a fantastic tool for planning and discovering systems and security audits Nmap. It allows novices to scan systems and enumerate hosts services and ports that are active. Its primary purpose is to scan networks and host services.
Features:
Scan at a super fast speed.
Maps advanced network attractions.
Compatible with multiple operating systems.
3. Metasploit Community Edition
Metasploit could be a broadly utilized entrance testing system. The community edition is free and culminates for tenderfoots to memorize vulnerabilities, misuses, and payloads. It's an intelligent way to see how aggressors can compromise frameworks and how to secure them.
Features:
Extensive library of exploits and payloads.
Easy-to-use graphical interface.
Ideal for practicing ethical hacking techniques.
4. Kali Linux
Kali Linux could be a Debian-based Linux dispersion particularly planned for entrance testing and security examination. Stuffed with a wide cluster of tools, it's a one-stop shop for anybody inquisitive about cybersecurity.
Features:
Pre-installed cybersecurity tools.
Lightweight and customizable.
5. Burp Suite Community Edition
Burp Suite may be a favorite among web application security analyzers. The community version is free and incorporates apparatuses for reviewing HTTP demands, analyzing web vulnerabilities, and understanding how web apps work.
Features:
Comprehensive suite for web vulnerability scanning.
User-friendly interface.
Supports learning about web security.
6. CyberChef
Known as "The Cyber Swiss Armed Force Cut," CyberChef may be a web-based tool for encryption, encoding, and information examination. Its instinctive drag-and-drop interface makes it perfect for apprentices investigating the essentials of cryptography and information change.
Features:
Simplifies data processing tasks.
Hundreds of available operations.
Accessible via a web browser
7. OWASP ZAP (Zed Attack Proxy)
OWASP Destroy is an open-source web application security scanner. It is a beginner-friendly apparatus to memorize approximately web vulnerabilities like SQL infusion, cross-site scripting (XSS), and more.
Features:
Automated vulnerability detection.
Supports manual testing.
Detailed reports and logs.
8. Hashcat
Hashcat may be a free watchword recuperation device that makes a difference to clients getting the significance of secret word security. It bolsters a wide assortment of hashing calculations and illustrates how powerless passwords can be split.
Features:
High-performance password cracking.
Supports GPU acceleration.
Multi-platform support.
9. Vega
Vega is another web security scanner that is well-suited for beginners. It's open source, free, and helps to identify vulnerabilities in web applications. Not very hard to figure out, but very helpful.
Such simple tools are most likely never going to help in things such as penetration testing.
XSS and SQL injection are some of the most common they get through to use the graphical interface they have.
10. ClamAV
ClamAV is another tool that most probably every cybersecurity deploys. Cross-platform functionality always plays a critical role for users as not only are they bound to a particular OS. In terms of the tools available, there is a command line option and also a Graphical User Interface.
Conclusion
Investing in these tools will give you a practical ability on how things work, from advanced systems analysis to web application security. Also, users must remember that these are ethical dilemmas and that all users need to comply with the laws of the land. It should make you better equipped to face the advancing technical era out there. So what are you waiting for, grab this opportunity. visit us Enbridg
0 notes